Protection is what you do after the alert...
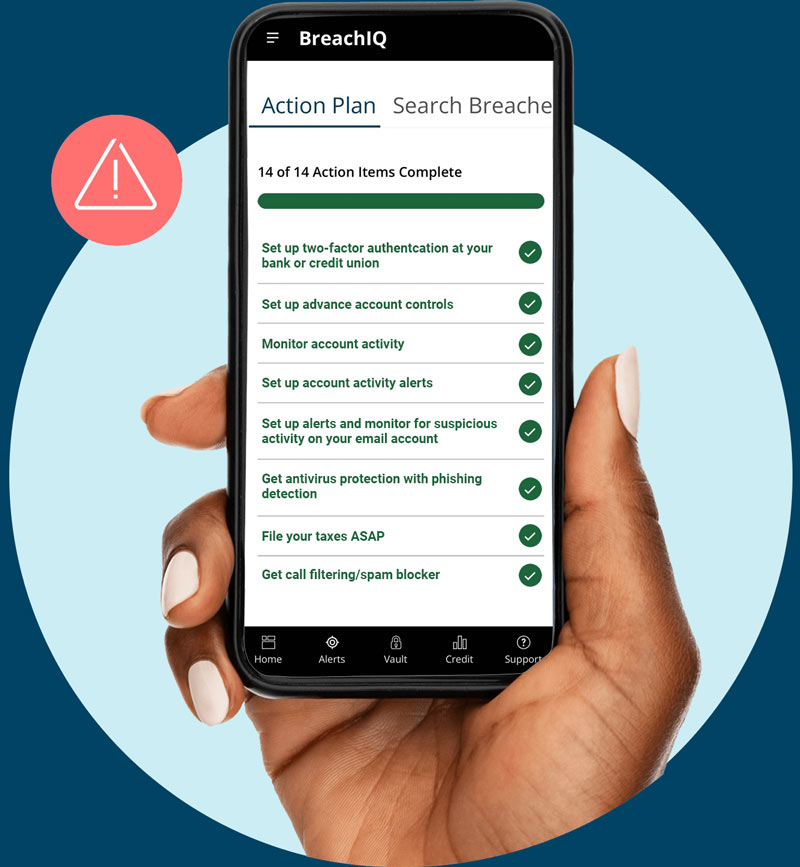
Get More Protection with a step-by-step Personalized Action Plan tailored to your Dark Web exposure.
66% of consumers claim they don’t know what to do to protect their identity, don’t be one of them.
(Source, TransUnion Consumer pulse survey, Q1 2023, n=2,282)
Your Identity is personal. So is your protection.
More Personalized
You get a Personalized Action Plan and Personalized Identity Safety Score based on your actual breach history.
More Informed
Unlimited access to daily TransUnion® credit reports and 24/7 Dark Web monitoring and alerts.
More Protected
Identity Monitoring, Fraud Prevention and Theft Recovery for You and Your Family.
Keep everyone in the house more protected with a family plan.
Comprehensive identity protection designed for you.
Your private data shouldn’t be free for the taking. Discover breaches that may have access to your credit details, PINs, passwords, medical records, family info and more.
- 24x7 Dark Web monitoring and alerts
- 3 bureau credit monitoring and alerts
- 3 bureau credit reports (Quarterly)
Beat identity theft––without the fight. Custom, straightforward response plans explain exactly how you regain control over your data if it’s stolen.
- Personalized Action Plan – your step-by-step guide to Identity Protection
- Online PC Protection
- Identity Vault
With dedicated restoration specialist and up to $2,000,000 ID theft insurance, we are here to restore your identity so you can get back to life.
- Dedicated Restoration Specialists
- Fully Managed Restoration
- Up to $2MM Insurance Policy in UltraSecure+Credit package and $1MM in UltraSecure
Identity theft is an expensive headache. Shielding yourself and your family doesn’t have to be.
Starting at $19.90 per month, get award-winning identity theft protection from a provider with 19 years experience.
- Individual Plans
- Family Plans
† Coverage varies in New York
†† All 3 national credit bureaus: TransUnion®, Experian®, and Equifax®
† Coverage varies in New York
†† All 3 national credit bureaus: TransUnion®, Experian®, and Equifax®
Recommended from leading identity theft protection review sites.



Frequently Asked Questions:
Whether you have our solution or not, here are some immediate steps you can take:
1. Lock down the problem account | If you know where the theft occurred, contact the organization, dispute the charges and ask to lock or close the account.
2. Sign up for a credit monitoring service if it is available to you | Over 400 million people were affected by a data breach in 2022. If you receive a breach alert, read it carefully. If it includes an offer of free credit monitoring, sign up.
3. Read credit card and bank statements to look for unauthorized charges | Review your active, dormant and infrequently used accounts. If you see anything amiss, contact your financial institution and work with them to safeguard your account.
4. Request a credit report from all three major reporting agencies | You’re entitled to at least one free credit report from each agency (TransUnion®, Experian® and Equifax®) per year, which you can request at the official site, AnnualCreditReport.com. Review your reports to look for any accounts you don’t recognize, which could indicate potentially fraudulent activity.
5. Contact the Federal Trade Commission | To file a report for a stolen identity, visit IdentityTheft.gov or call 1-877-ID-THEFT (438-4338). For credit card fraud, in which only a single account was compromised, an FTC report may not be warranted.
6. Call your local police department to file a report | Notify your local law enforcement agency and file a police report. Have your identity theft report from the FTC on hand when you do so. The police report will be an important document to have when dealing with banks, credit agencies and potential bill collectors.
7. Request fraud alerts from the three major credit bureaus | Contact one of the national credit reporting agencies to place a fraud alert on your file. This alert will make it more difficult for new credit applications to be accepted without additional verification. The notice stays on your record for one year, giving you time to work on clearing your name. You can also renew the alert once the initial year is up.
For an added layer of protection, you can freeze your credit, which blocks third parties whose use is not exempt under law from accessing your credit report. This can reduce the chance that a new account can be opened in your name. It’s free to freeze and unfreeze your credit, and it won’t affect your credit score.
8. Implement the following preventative security measures | Adopt these proven protective habits:
- Create strong passwords and use unique passwords for each account — do not use the same password for multiple accounts.
- Shred documents with personal information when disposing them.
- Keep personal information (i.e. address, phone number, etc.) off social media sites, as well as any details you use for online security questions, like your mother’s maiden name.
- Avoid carrying your Social Security card in your wallet.
When enrolling in our identity protection service, you can opt to enroll your children, which protects their future credit scores and personal information. Features include:
- Comprehensive child identity monitoring so you’re aware of changes to your child’s records or if fraudsters are wrongfully using their information.
- Fully managed restoration services from our Restoration Team.
- Up to $2 million identity theft insurance policy.
Learn more about the harmful effects of child identity theft and some simple steps you can take at home to protect their personal information.
You can add dependent children through the Dashboard under My Account / Family Protection, or you can contact Member Services at memberservices@identityforce.com or 877-694-3367.
Our team will reach out to you and we won’t close your case until both you and a Restoration Representative agree that the existing case has been resolved. Otherwise, the case stays open and we’ll keep working to resolve it. If fraudulent activity reappears on a closed case and your membership is still active, we’ll reopen the case and reactivate our Restoration services.
Here are just some of the services we provide to deliver the assurance, confidence, and increased protection we all need in today’s digitized world:
- Timely alerts when a hard inquiry of your credit report is requested.
- Continuous monitoring of your medical accounts.
- Comprehensive monitoring of your Social Security number, email address and phone numbers in places where they should not be listed, including the dark web and online forums where criminals trade stolen information.
- Alerting you of changes in your address, court records in your name and payday loans taken out in your name.
- Notification of significant data breaches, including an easy-to-understand risk score.
The credit scores provided are based on the VantageScore® 3.0 model. Lenders use a variety of credit scores and are likely to use a credit score different from VantageScore® 3.0 to assess your creditworthiness.


